Currently building a small service that has the need of multitenancy and where each user can be part of multiple tenants and have different permissions at each tenant. One solution could be to e.g. have multiple realms in a KeyCloak installation or perhaps make use of custom user attributes etc. Could potentially also solve it with an external IDP service that allows for custom DB integration or similar, but there's also a "wish" to not be too tied up to an external IDP, so a "simple" integration is preferred. The design decision then was "authenticate externally, authorize locally".
Edit: Follow up post: "The Journey with multi-tenancy accesses continues with some issues"
It's still work in progress, but the idea is something like this
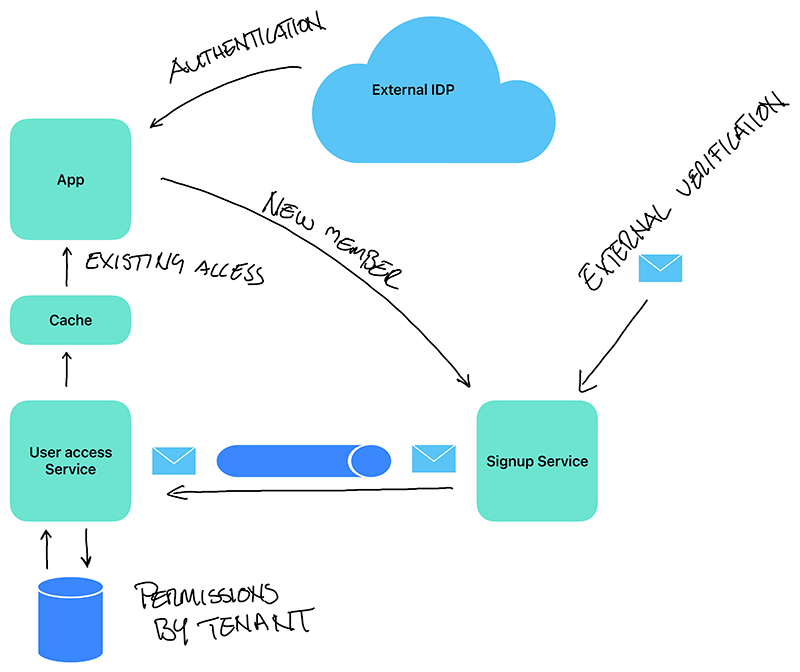
No user credentials will be handled within the applications boundaries. All of that is handled externally and the external IDP only provides the application with tokens that are verified against IDP keys, certificates etc. In case it's a new member, an asynchronous sign up process takes place. The user still doesn't have any access until the external user verification (e.g. via email) has taken place. Upon that confirmation, user accesses are setup and the user can now start using the system.
The Signup service uses a SAGA construct that makes use of timeouts. So if no external verification is done within a certain time period, the SAGA is finalized and all data is removed.
The Cache with user accesses never spans longer than the tokens validity. Furthermore, it will be invalidated upon any writes affecting the accesses.
Work in progress. Will see where it ends up.
//Daniel
